Table of Contents
Researchers identified a new Chinese spying campaign targeting a Southeast Asian government, especially the Ministry of Foreign Affairs. Attackers have used spear-phishing techniques to implant the previously unknown backdoor on Victims. Further analysis reveals that attackers have used old Microsoft Office exploits and loaders with anti-analysis and anti-debugging techniques to access the victim’s machines.
Who Is Behind This New Chinese Spying Campaign?
Several facts made researchers suspects that this new Chinese spying campaign has been linked to a Chinese advanced persistent threat (APT) group “SharpPanda”.
Targets of This New Chinese Spying Campaign?
As we said earlier, these surveillance operations were seen targeting the Southeast Asian Government, interestingly more on the Ministry of Foreign Affairs department. Attackers were not just interested in spying on the official assets but also tried targeting the victim’s personal assets to gather more as much information as they can. Moreover, researchers warn that this spying campaign could be expanded to other targets around the world.
How Is This New ‘Chinese Spying Campaign’ Operated?
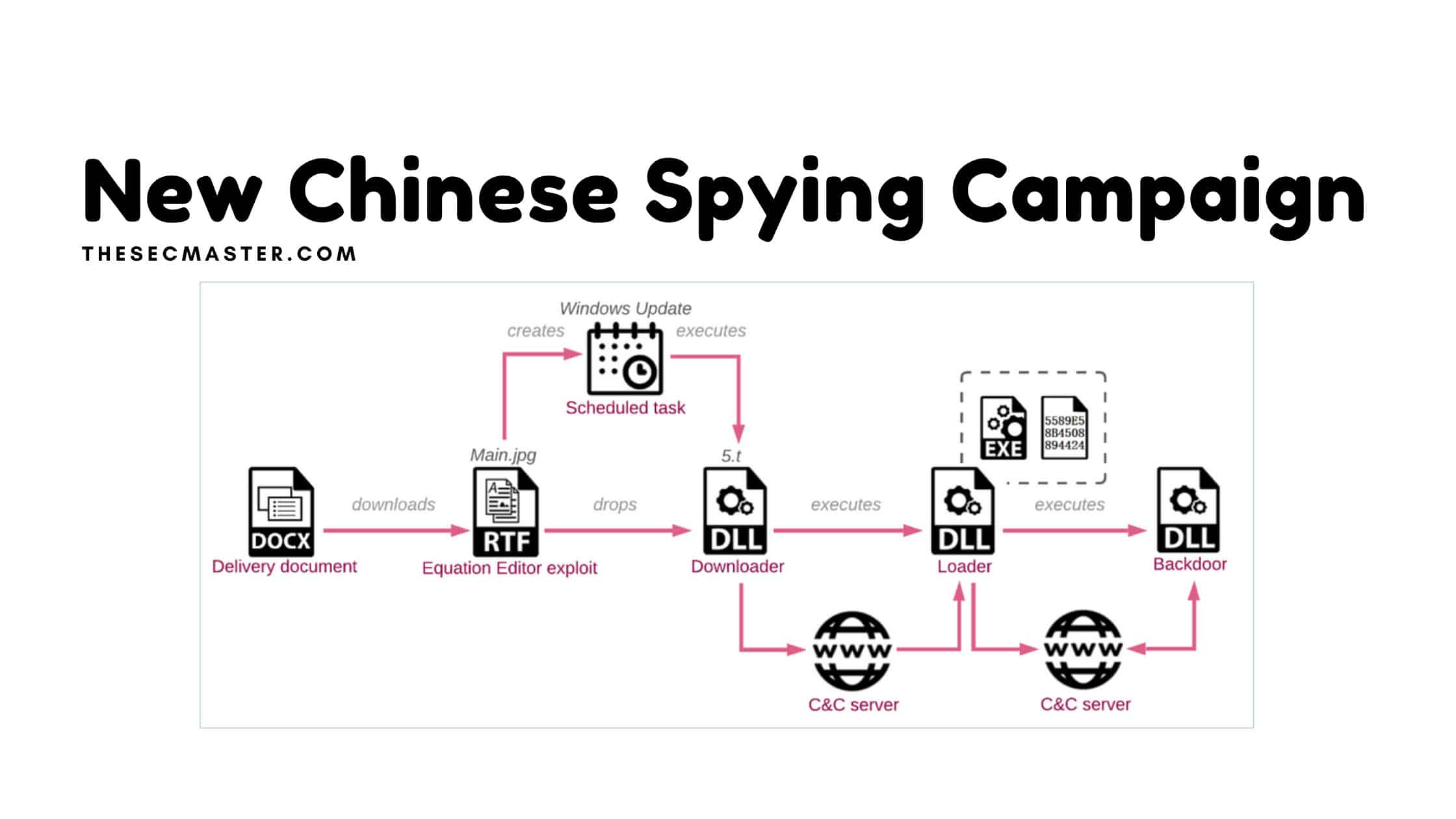
Threat actors weaponize a DOCX file which impersonates official document from other departments of the government.
That fake government document would be delivered to multiple members of the Ministry of Foreign Affairs using various social engineering techniques.
When the person opens the document, the document will download a new next-level payload from the attacker’s remote server that contains an encrypted downloader. The downloader is an RTF file weaponized using a variant of a tool named RoyalRoad. A tool used to create custom Microsoft documents with embedded objects. Attackers used this tool to load the exploits of Microsoft Word. Threat actors decrypt the RTF file using the RC4 algorithm with the key 123456. The decrypted file is saved as 5.t in the %Temp% folder. Research revealed that the 5.t file creates the scheduled task named Windows Update that should run the exported function StartW from 5.t with rundll32.exe, once a day.
The downloader (5.t) will start sharing information with the attacker’s remote server “HTTPS://<C&C IP>/<working_folder>/Main.php?Data=<encrypted_data>” and subsequently responds back with a shellcode loader “HTTPS://<C&C IP>/<working_folder>/buy/<hostname>.html”. The downloader can gather information such as the victim’s computer hostname, OS name, and version, system type (32/64 bit), user name, MAC addresses of the networking adapters. It also capable of querying WMI for anti-virus detection.
At the last phase of the attack, the loader connects with the remote server from where an implant a backdoor dubbed “VictoryDll_x86.dll” will get downloaded and executed. Click here to read the full analysis.
This backdoor is capable of doing many operations like:
Delete/Create/Rename/Read/Write Files and get files attributes
Get processes and services information
Get screenshots
Pipe Read/Write – run commands through cmd.exe
Create/Terminate Process
Get TCP/UDP tables
Get CDROM drives data
Get registry keys info
Get titles of all top-level windows
Get victim’s computer information – computer name, user name, gateway address, adapter data, Windows version (major/minor version and build number), and type of user
Shutdown PC
Backdoor Commands
| Message Type | Type ID | Arguments | Source |
| Send victim’s information | 0x2 | Info | Victim |
| CDROM drives data | 0x4 | – / Drives data | Both |
| Get Files data | 0x5/0x6 | Path / Files data | Both |
| Create Process | 0x7 | Command Line | C&C server |
| Rename File | 0x8 | Old filename, New filename | C&C server |
| Delete File | 0x9 | Filename | C&C server |
| Read File | 0xa | Filename, Offset / File’s content | Both |
| Exit Pipe | 0xb | – | C&C server |
| Create Pipe | 0xc | – | C&C server |
| Write To Pipe | 0xd | Buffer | C&C server |
| Get Uninstalled software data | 0xe | – / Software data | Both |
| Get windows text | 0xf | – / Windows text | Both |
| Get active processes data | 0x10 | – / Processes data | Both |
| Terminate Process | 0x11 | Process ID | C&C server |
| Get screenshot | 0x12/0x13 | – / Screenshot temp file | Both |
| Get services data | 0x14 | – / Services data | Both |
| Get TCP/UDP tables | 0x15 | – / Tables data | Both |
| Get registry key data | 0x16 | Registry path / Reg data | Both |
| Shutdown | 0x17 | – | C&C server |
| Exit process | 0x18 | – | C&C server |
| Restart current process | 0x19 | – | C&C server |
| Write to file | 0x4C7 | Filename, Buffer | C&C server |
| Start Connection | 0x540 | Zero Byte | Victim |
| Get victim’s information/Update XOR key | 0x541 | New XOR key / Victim’s info | Both |
| None | 0x120E | – | C&C server |
| Ack | 0x129D3 | Name (‘admin’ in our case) | Victim |
Indicators of Compromise
Documents
278c4fc89f8e921bc6c7d015e3445a1cc6319a66
42be0232970d5274c5278de77d172b7594ff6755
f9d958c537b097d45b4fca83048567a52bb597bf
fefec06620f2ef48f24b2106a246813c1b5258f4
548bbf4b79eb5a173741e43aa4ba17b92be8ed3a
417e4274771a9614d49493157761c12e54060588
Executables
03a57262a2f3563cf0faef5cde5656da437d58ce 5.t
388b7130700dcc45a052b8cd447d1eb76c9c2c54 5.t
176a0468dd70abe199483f1af287e5c5e2179b8c 5.t
01e1913b1471e7a1d332bfc8b1e54b88350cb8ad loader
8bad3d47b2fc53dc6f9e48debac9533937c32609 ServExe (x64)
0a588f02e60de547969d000968a458dcdc341312 VictoryDll
C&C servers
45.91.225[.]139
107.148.165[.]151
45.121.146[.]88
Old backdoor versions
MClient:
aa5458bdfefe2a97611bb0fd9cf155a06f88ef5d
4da26e656ef5554fac83d1e02105fad0d1bd7979
f8088c15f9ea2a1e167d5fa24b65ec356939ba91
0726e56885478357de3dce13efff40bfba53ddc2
7855a30e933e2b5c3db3661075c065af2e40b94e
696a4df81337e7ecd0ea01ae92d8af3d13855c12
abaaab07985add1771da0c086553fef3974cf742
7a38ae6df845def6f28a4826290f1726772b247e
Autostart_DLL:
e16b08947cc772edf36d97403276b14a5ac966d0
c81ba6c37bc5c9b2cacf0dc53b3105329e6c2ecc
a96dfbad7d02b7c0e4a0244df30e11f6f6370dde
6f5315f9dd0db860c18018a961f7929bec642918
Conclusion:
Researchers discovered that this Chinese spying campaign has been active for more than three years. And this campaign could be expanded to other targets around the world.
If you find this interesting please read more interesting articles here:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.