Table of Contents
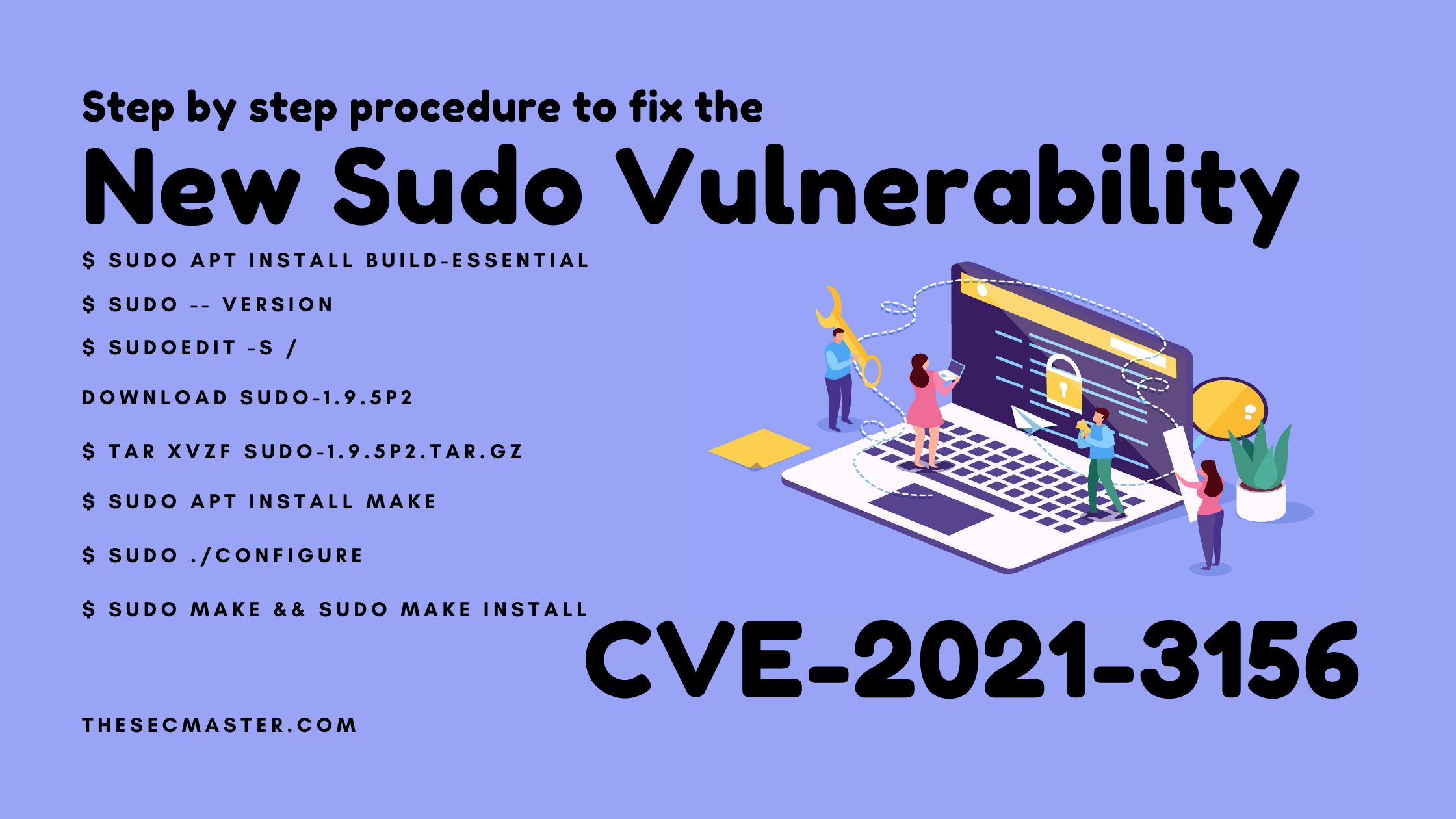
Step By Step Procedure To Fix The New Sudo Vulnerability (CVE-2021-3156)
You might have recently read about a new heap overflow vulnerability (CVE-2021–3156) on Sudo discovered by a team of security researchers from Qualys. This article covers not just information about vulnerability. It covers how to find the vulnerable host and how to fix the new sudo vulnerability found on a vulnerable host.
What Is Sudo?
I am afraid if someone doesn’t know about sudo. Sudo is the most powerful, open-source, ubiquitous utility used in all non-windows platforms like Unix, Linux, Solaris, and Mac. sudo allows users to run the programs with another user’s security privileges, by default ‘superuser’.
About the New Heap Overflow Sudo Vulnerability (Cve-2021–3156):
This vulnerability allows an unprivileged user to gain root privileges without authentication after successfully exploiting the vulnerable host. Qualys research team reported that they have succeeded in obtaining complete root privileges by exploiting the vulnerability on Ubuntu 20.04 (Sudo 1.8.31), Debian 10 (Sudo 1.8.27), and Fedora 33 (Sudo 1.9.2). On the latest note, they also confirmed that the vulnerability is prone to macOS, AIX, and Solaris as well. Quays confirmed that they have developed multiple variants of exploits and testthem ed independently on each one of those operating systems. You can see the Proof of Concept and other technical details on the Qualys website if you need to know how to find the vulnerability on a host and patch it. Please follow us on this article and read below two sections to know how to find and fix the new sudo vulnerability.
Further to say, This vulnerability has been registered in mitre on 26th Jan 2020. It has been assigned CVE-2021–3156 in the Common Vulnerabilities and Exposures database. sudo confirmed that this vulnerability affected to sudo versions 1.7.7 to 1.7.10p9, 1.8.2 to 1.8.31p2, and 1.9.0 to 1.9.5p1.
Technical Details of the New Sudo Vulnerability (Cve-2021–3156):
Todd C. Miller, a sudo maintainer, said “When sudo runs a command in shell mode, either via the -s or -i command line option, it escapes special characters in the command’s arguments with a backslash. The sudoers policy plugin will then remove the escape characters from the arguments before evaluating the sudoers policy (which doesn’t expect the escape characters) if the command is being run in shell mode. A bug in the code that removes the escape characters will read beyond the last character of a string if it ends with an unescaped backslash character. Under normal circumstances, this bug would be harmless since sudo has escaped all the backslashes in the command’s arguments. However, due to a different bug, this time in the command-line parsing code, it is possible to run sudoedit with either the -s or -i options, setting a flag that indicates shell mode is enabled. Because a command is not actually being run, sudo does not escape special characters. Finally, the code that decides whether to remove the escape characters did not check whether a command is actually being run, just that the shell flag is set. This inconsistency is what makes the bug exploitable.”
How to Find the New Sudo Vulnerability (Cve-2021–3156) On the Host?
Check your host is running one of these affected Sudo versions:
1.7.7 through 1.7.10p9
1.8.2 through 1.8.31p2
1.9.0 through 1.9.5p1
Use this command to check the version of Sudo your host is running:
$ Sudo — version
In our case, our host is having 1.8.31, which is the vulnerable version.
This image is captured by the author
Suppose you want to confirm your sudo version is vulnerable to this flaw. Try this command:
$ sudoedit -s /
If your host is running a vulnerable version of sudo. You will see this on your terminal.
sudoedit: /: not a regular file
If your host is running a patched version of sudo. You will see this on your terminal.
usage: sudoedit [-AknS] [-C num] [-D directory] [-g group] [-h host] [-p prompt] [-R directory] [-T timeout] [-u user] file …
Let’s try this method on our host and find out whether our host is running a vulnerable version.
As soon as we enter the command, we have prompted to enter a password.
If the sudoers plugin has been patched but the Sudo front-end has not, the following error will be displayed :
Sudoedit: invalid mode flags from Sudo front end: 0x20002
Patching either the Sudo front-end or the sudoers plugin is sufficient to prevent exploitation, but applying the complete patch is the safest approach.
How to Fix the New Sudo Vulnerability (Cve-2021-3156) On the Host?
Time needed: 10 minutes.
Commands required to fix the new Sudo vulnerability (CVE-2021-3156)
Check the version of Sudo
$ sudo — version
Make sure your Sudo version is vulnerable to the exploit
$ sudoedit -s /
Download the patched Sudo 1.9.5p2 version
Extract the downloaded file
$ tar xvzf sudo-1.9.5p2.tar.gz
Install the make utility
$ cd sudo-19.5p2
$ sudo apt install makeInstall the build-essential packages.
$ sudo apt update
$ sudo apt install build-essentialConfigure all the files inside the Sudo directory
$ sudo ./configure
Compile and install the downloaded Sudo 1.9.5p2 utility
$ sudo make && sudo make install
Sudo.ws has fixed this vulnerability in the newly released versions: Sudo 1.9.5p2, released on 26 Jan 2021.
Download the patched sudo 1.9.5p2 version from the site using the wget utility.
$ wget https://www.sudo.ws/dist/sudo-1.9.5p2.tar.gz
This image is captured by the author
Since it is a compressed file use the tar utility to extract it.
$ tar xvzf sudo-1.9.5p2.tar.gzAfter extracting it.
A directory gets created ‘ sudo-1.9.5p2’.
This image is captured by the author
‘make’ utility is mandatory to compel and install the Sudo utility. Install the make utility if you didn’t have it on your host.
$ cd sudo-19.5p2
$ sudo apt install make
In our case, our host system has the latest version of make.
This image is captured by the author
Then type this command on the terminal. This command lets to check and configure all the files inside the Sudo directory.
$ sudo ./configure
Our host system threw an error. from reading the error message we can tell that we have some issues with the GCC compiler. We can’t go ahead by bypassing this process. Let’s fix this issue first.
This image is captured by the author
Debian family Linux has a repository that has a meta package called ‘build-essential’ which has a collection of GNU compiler, GNU debugger, and other development libraries and tools required to compile software. Use these commands to install the build-essential packages.
$ sudo apt update
$ sudo apt install build-essential
This image is captured by the author
This image is captured by the author
This image is captured by the author
After installing the build-essential packages. Let’s jump back to the process and try running the make configurations command again.
$ sudo ./configure
This time it ran. We didn’t encounter the issue that we had last time.
This image is captured by the author
We are almost at the end. The final important step is to compile and install the downloaded Sudo 1.9.5p2 utility. Try this command to do that.
$ sudo make && sudo make install
This image is captured by the author
That’s all. Exit from this terminal window. Fire up a new terminal and check the Sudo version.
This image is captured by the author
Let’s verify the host is vulnerable to the exploit. Repeat the verification steps shown in the previous section. Check what would be the output of the
$ sudoedit -s /
A patched version of Sudo will simply display a usage statement, for example:
usage: sudoedit [-AknS] [-C num] [-D directory] [-g group] [-h host] [-p prompt] [-R directory] [-T timeout] [-u user] file …
This image is captured by the author
We successfully patched the host.
Note: Those who want to automate this process. Make sure build-essential packages are installed on all your host systems.
Thanks for supporting our work. Please check-in
Thanks for supporting our work. Please check thesecmaster.com for more such tutorials.
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.