Table of Contents
Security Researchers Released Detail Analysis On DarkSide Ransomware Attacks
Security researchers have released a detailed
of DarkSide ransomware attacks. The DarkSide campaign uses customized ransomware executables for different targets with Salsa20 with the custom matrix and RSA-1024 encryption algorithms. The operators behind the DarkSide ransomware harvest the data in clear text from the victim’s server before encrypting it. The plain text data stolen is then uploaded to DarkSide’s leak website, which is used as a powerful extortion tool. Let’s see what analysis tells about the DarkSide ransomware attacks in this article.
What Is The DarkSide Ransomware?
“Ransomware is designed to encrypt the victim’s files to extort and ransom for their recovery. DarkSide is a ransomware-as-a-service(RaaS)–the developers of the ransomware received a share of the proceeds from the cybercriminal actors who deploy it, known as “affiliates.” This DarkSide ransomware variant executes a dynamic-link library (DLL) program used to delete Volume Shadow copies available on the system. The malware collects, encrypts, and sends system information to the threat actor’s command and control (C2)domains and generates a ransom note to the victim.
According to the analysis of DarkSide ransomware attacks, the malware collects information which includes the operating system, username, hostname, domain, default language, and operating system (OS) architecture.
Where Does DarkSide Ransomware Originate?
In Aug 2020, the DarkSide ransomware group announced RaaS (Ransome as a Service) through a press release. They are running the DarkSide Inc like a professional organization. They call their victims ‘clients’. They provide web chat support to victims to recover their data. The group will carry out a detailed analysis of the victim’s financial data before the attack to set the ransom amount.
The research also revealed that Darkside’s malware would check victim’s device language settings to ensure they don’t attack Russia-based organizations. They have posted about their interests in hiring Russian-speaking partners in many Q&A forums. This would make the world think that the DarkSide ransomware could be originated in Russia.
Did DarkSide Get The Ransom?
Picture #1: DarkSide ransomware attack message
Yes. DarkSide ransomware drops a text note with the name ‘README.<UniqueID>.TXT’ in each encrypted directory. The note contains the instructions for the user to recover files. Here you can see an example of recovery instructions. The note just tells about the recovery process. You may not see about the ransom demand. DrakSide has no standard ransom policy. It all depends on the type of victim. They have made a public announcement that hospitals, schools, non-profits, and governments are not in their attack interest. However, they try targeting big organizations that can afford to pay large ransoms.
Picture #2: DarkSide ransomware attack message
What Stealth Techniques Used In DarkSide Ransomware Attacks?
DarkSide ransomware attack campaigns are known for their stealth techniques to evade detection. Some common stealth techniques are:
They use TOR to communicate with C2 servers.
The large waiting period to work under the radar.
Avoid action during EDR scans.
DarkSide uses a custom host, connections, and code for each victim.
Deleting its own logs for detection protection.
Code obfuscation.
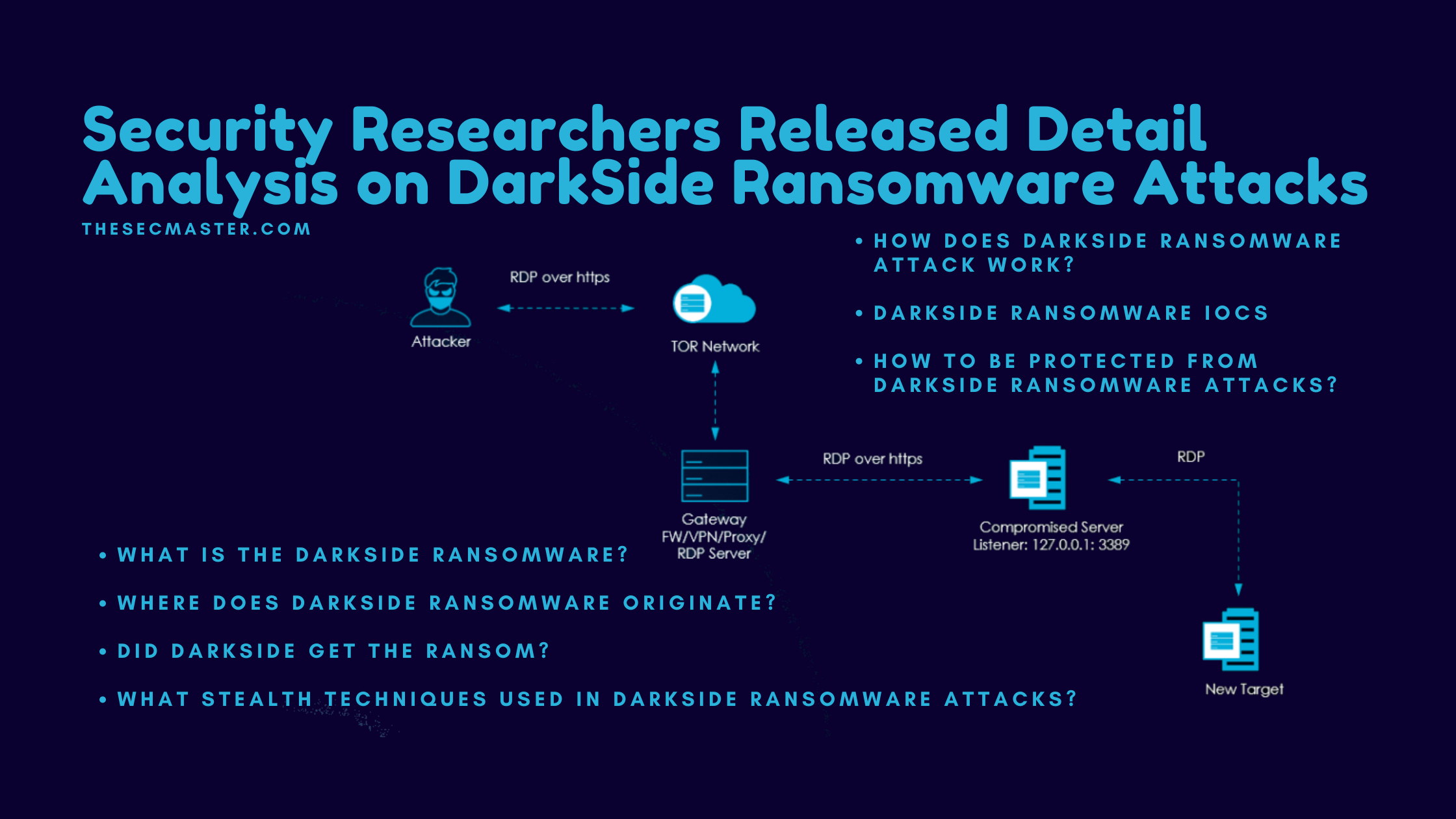
How Does DarkSide Ransomware Attack Work?
The anatomy of DarkSide ransomware attacks is not simple enough to tell. DarkSide ransomware uses custom codes, payloads, tools, and tactics with different victims. We tried to describe its work in simple steps. If you want to see the DarkSide ransomware attacks in detail, please visit this page.
Attackers initially find the week targets to enter the network like unpatched internet-facing VDIs, compromised accounts, RCE vulnerabilities, and servers.
After compromise, attackers quickly deploy an additional RDP on the compromised servers to preserve access even after patching the server.
Attackers then install TOR clients on the compromised servers to set up communication with C2 servers primarily through RDP over HTTPS over TOR. It’s also seen that attackers have used Cobalt Strike to set up communication with C2 servers as a secondary way of communication.
Upon setting up the connection with C2 servers, attackers start the exfiltration process. They try harvesting credentials stored in files, in memory, and on domain controllers.
All the data exfiltrated will be sent to C2 servers over an encrypted channel.
DarkSide Ransomware IOCs:
IP Addresses:
176[.]103[.]62[.]217
99[.]83[.]154[.]118
Domains:
baroquetees[.]com
rumahsia[.]com
Hashes:
156335b95ba216456f1ac0894b7b9d6ad95404ac7df447940f21646ca0090673 (156335b95ba216456f1ac0894b7b9d…)
3ba456cafcb31e0710626170c3565aae305bc7c32a948a54f0331d0939e0fe8a (045621d9.BMP)
f6fba207c71d1f53f82d96a87c25c4fa3c020dca58d9b8a266137f33597a0b0e (README.045621d9.TXT)
How To Be Protected From DarkSide Ransomware Attacks?
We recommend following these best practices to strengthen the security poster.
Keep Anti-malware solutions at the endpoint and network-level updated at all times.
Keep the OS patches up to date.
Avoid accessing files or URL links in emails, chats, or shared folders from untrusted sources.
Disable the file sharing and printer services where ever needed. Or else implement strong authentication to use these services.
Don’t add the users to default admin groups.
Impose user restrictions on install and run unwanted software applications.
Ensure a strong password policy with regular password expires.
Educate your employees/contractors with phishing awareness training.
Implement URL and content filtering.
Deploy Endpoint Detection & Response (EDR) tools to detect the latest malware and suspicious activities on endpoints.
Block the usage of external storage media.
Thanks for reading this post. Would you please visit our site to read more interesting articles on new threats and malware? Would you please share this article and help in creating awareness?
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.