Table of Contents
OpenSSL is a versatile command-line tool that allows you to work with SSL certificates, CSRs (Certificate Signing Requests), and private keys right from your terminal. In this post, we will show you how to check and verify the details of certificates, CSRs and private keys with OpenSSL.
Why Validate SSL Certificates, CSRs and Keys?
There are a few reasons why you may want to validate and inspect SSL certificates, CSRs and private keys using OpenSSL:
Debugging SSL Issues: If you are facing “certificate not trusted” errors or issues with key mismatches, OpenSSL can help you debug by inspecting certificates and keys.
Troubleshooting Renewals: When renewing SSL certificates, you can use OpenSSL to verify that the new CSR and private key match the existing certificate.
Validating Chains: OpenSSL allows you to validate certificate chains to ensure your certificate chain is properly formed.
Inspecting Certificates: OpenSSL makes it easy to view certificate contents like subject, issuer, validity period, etc. to verify certificate details.
Checking Keys: Private keys can be checked for consistency to detect corruption or key mismatch issues.
How to Check an SSL Certificate?
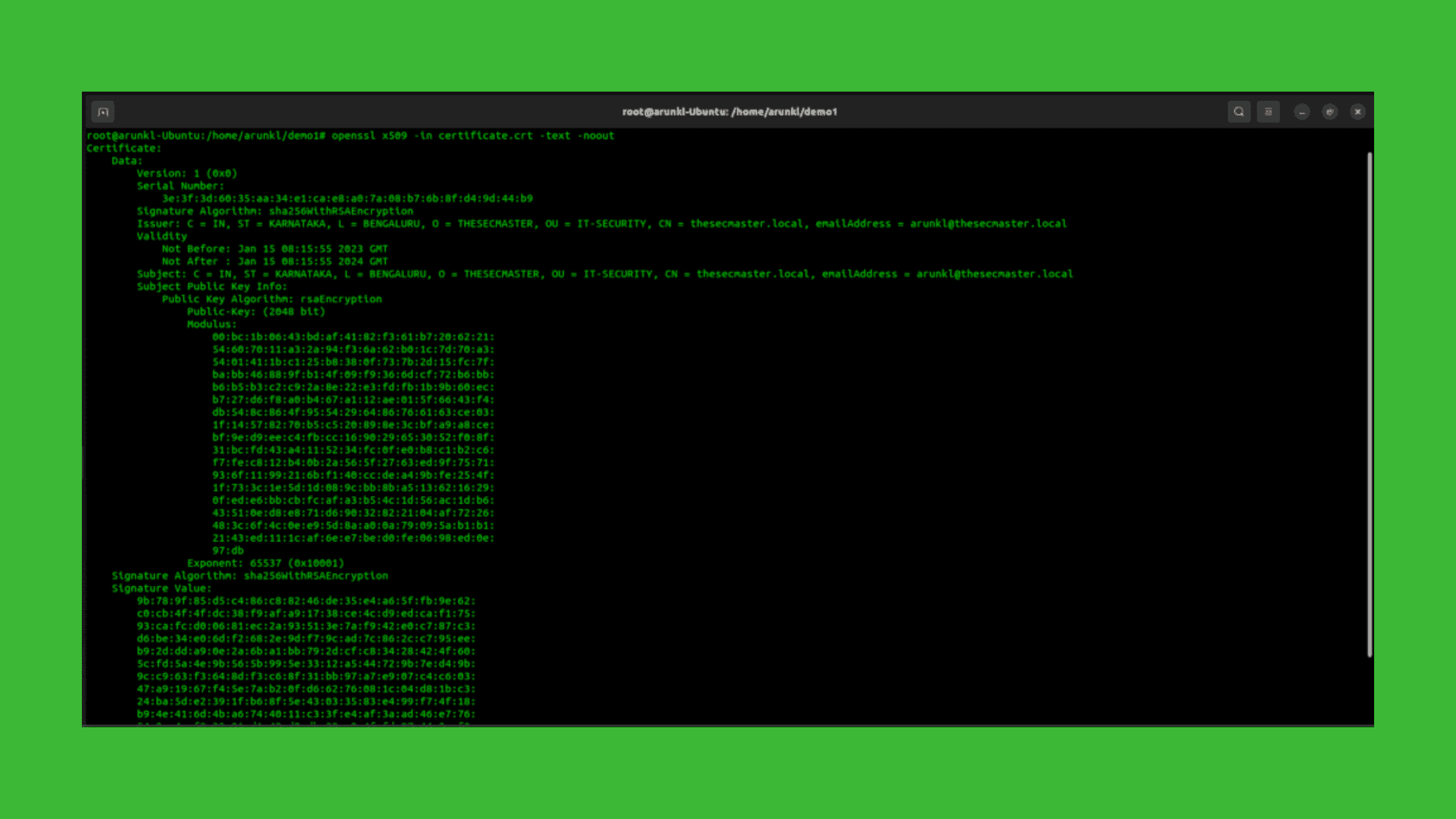
To check the contents of an SSL certificate in CRT or PEM format, use the following OpenSSL command:
openssl x509 -in certificate.crt -text -nooutThis will display all the certificate contents in a human-readable format including:
Subject attributes like common name, organization name etc.
Issuer attributes
Public key type and parameters
Signature algorithm
Serial number
Validity period (not before and not after dates)
Key usage extensions
Subject alternative names
Authority key identifier
Thumbprints/Fingerprints
Here’s a sample output:
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
13:57:eb:34:74:6d:59:eb:63:23:7b:47:9b:c3:1b:1e:66
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=US, ST=SomeState, L=SomeCity, O=SomeOrg, OU=SomeOU, CN=SomeCN
Validity
Not Before: Dec 5 00:00:00 2019 GMT
Not After : Dec 5 23:59:59 2020 GMT
Subject: C=US, ST=SomeState, O=SomeOrg, CN=example.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:b9:5d:51:28:e7:6c:61:16:91:65:81:4e:ce:7e:
c9:0a:10:95:24:b2:09:b8:5c:21:b9:ef:69:a3:4a:
62:73:8a:c4:bc:4d:4d:14:36:d0:67:1c:9e:77:6a:
7b:08:e5:d4:22:e2:93:55:13:f3:c5:35:7f:94:b3:
34:73:4a:92:58:55:b1:07:6d:67:70:6b:13:f2:f9:
d9:b3:1f:2f:c7:0c:b6:ee:e9:f1:14:3f:24:bd:6f:
d3:8f:05:ab:bb:7f:62:1a:48:a8:7f:0c:44:93:f7:
f9:29:8b:12:2b:61:00:e9:0e:8f:1b:d6:d1:5a:85:
0e:dc:c3:7e:b2:f9:b3:35:34:e9:b1:91:bc:e9:58:
c2:4f:27:16:98:d4:36:04:ce:c8:d7:2f:92:50:c9:
84:5d:62:c4:77:9b:60:04:16:09:04:7d:b8:64:74:
55:05:39:42:6c:90:18:b6:66:f0:88:15:40:93:cc:
d7:e7:b3:cc:48:55:25:0c:f8:da:7e:f2:cd:4e:70:
21:f3:69:2a:9c:8b:77:6d:ee:21:46:2c:46:b5:15:
12:65:32:04:a8:6e:5a:04:2f:24:5b:8f:3c:6c:c8:
c7:3b:b7:bb:e9:03:5f:50:be:7a:f3:31:1b:13:c1:
b6:31:4e:04:6f:c2:df:f6:45:97:94:0f:47:72:df:
bb:8b
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Subject Key Identifier:
B4:B0:5E:C9:45:77:A5:75:27:E1:F7:3D:28:D7:7E:49:4E:E2:99:89
X509v3 Authority Key Identifier:
keyid:86:28:8F:F6:F2:73:20:57:54:CF:95:57:0F:A7:C5:F1:2F:E2:61:D0
DirName:/C=US/ST=SomeState/L=SomeCity/O=SomeOrg/OU=SomeOU/CN=SomeCN
serial:AF:92:88:A0:DF:AA:59:5D
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 Key Usage:
Digital Signature, Key Encipherment
X509v3 Subject Alternative Name:
DNS:example.com, DNS:www.example.com
Signature Algorithm: sha256WithRSAEncryptionHow to Check a CSR?
To verify and view the contents of a certificate signing request (CSR), you can use the following openssl command:
openssl req -text -noout -verify -in example.csrThis will display details like subject, public key, attributes etc. included in the CSR.
Here’s some sample output:
Certificate Request:
Data:
Version: 1 (0x0)
Subject: C=US, ST=SomeState, L=SomeCity, O=Example LLC, CN=example.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:cb:0c:0a:26:4d:8a:2a:35:ad:19:cd:7f:b2:fe:
54:ff:75:27:e7:62:66:12:8f:2b:6b:b3:0c:4f:05:
08:15:8a:5a:7b:54:17:ef:49:5f:5c:7a:65:4f:18:
e0:31:7a:7a:71:df:f5:96:a3:7c:b0:6c:a2:c0:78:
cc:5e:d3:4a:06:a3:40:29:0e:f5:09:dd:a6:a2:ee:
24:cc:4d:16:4c:e9:73:df:fe:41:81:7b:23:a9:32:
b7:94:9a:a9:88:7d:00:3a:1d:00:d6:ab:7f:1f:72:
8b:f8:5e:c8:f1:f9:21:29:e1:2b:4d:47:59:11:7b:
0d:8c:8e:3a:07:20:5c:12:bd:fe:15:54:d1:76:b7:
b5:01:54:99:22:72:32:cf:b0:19:f3:03:b6:1a:f2:
56:2e:94:2d:ad:63:3d:e6:66:3c:07:6c:46:44:36:
91:7d:7c:83:8c:9b:2d:8f:57:2d:dc:f0:31:05:2f:
99:64:3b:87:55:76:80:ea:7e:33:0c:85:68:95:69:
81:7f:81:c4:ac:b2:b0:27:8c:6b:70:81:5d:da:4d:
7d:f3:20:b3:1a:a4:a5:cd:7a:a0:21:45:43:59:42:
3a:86:0f:68:b2:ee:35:6c:00:e9:04:01:5f:31:ab:
a7:16:d8:65:70:02:9e:e8:b4:4d:b8:75:8b:bf:35:
1c:ce
Exponent: 65537 (0x10001)
Attributes:
Requested Extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Key Usage:
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 Subject Alternative Name:
DNS:example.com, DNS:www.example.com
Signature Algorithm: sha256WithRSAEncryptionHow to Check a Private Key?
Private keys can be checked using OpenSSL to detect any inconsistencies or corruption issues. To check a private key in PEM/KEY format, use the following openssl command:
openssl rsa -in private.key -checkThis will do an integrity verification of the private key and confirm whether the key is valid or not. If the key is encrypted/password protected, you need to decrypt it first before checking using:
openssl rsa -in private.key -out decrypted.key
openssl rsa -in decrypted.key -checkThis will decrypt the key into a plaintext file, and then the check can be done. On success, you will see ‘RSA key ok’ message. Any errors indicate issues with the private key.
Conclusion
OpenSSL provides a powerful command-line interface to validate and troubleshoot SSL certificates, CSRs and private keys right from your terminal. Knowing these basic OpenSSL commands can help debug SSL issues, renewals, validate chains and inspect keys/certs easily. For more OpenSSL examples and tutorials, check out the Most Common OpenSSL Commands guide.
Thanks for reading this post. Please share this post and help secure the digital world. Visit our website, thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram and subscribe to receive updates like this.
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.